Programmatic Multi Factor Auth and Time Based One Time Passwords
We’re Earthly. We simplify and speed up software building using containerization. Earthly is perfect for automating your build processes and ensuring reliable builds. Check it out.
“You need to setup multi-factor authentication.”
This is what I was told. I already had a YubiKey, but I wasn’t using it for my AWS credentials and this was not smart. So many AWS accounts get compromised without MFA:
Previously, I’d had a slightly bad time with YubiKeys: My computer fell and crushed my key. MFA is great until you lose an F. But Alex gave me a great solution to this problem – securely store the MFA secret key.
Side Note: You Should MFA
If you have something valuable online, something that can be stolen or turned into bitcoin you should set up multi-factor authentication for it.
(FYI: Previously this was often called 2FA, two-factor-authentication.)
MFA Setup in AWS
So here is what I did.
I set up a virtual MFA device in AWS and before adding it to google authenticator on my phone, using the QR code, I grabbed the secret key and stored it somewhere secure.
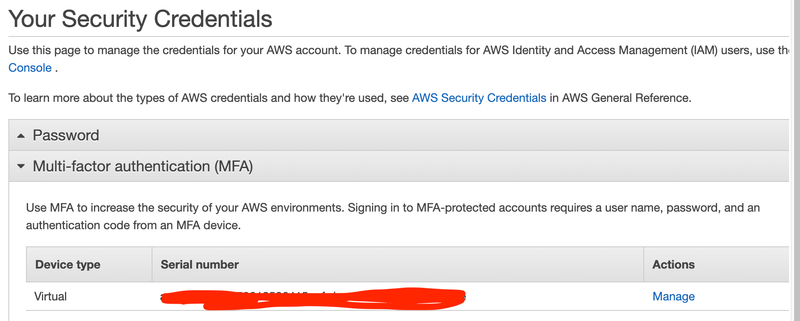
I stored it in LastPass but it could have been stored on paper in a safe, or in Earthly Secrets. This Virtual MFA secret key needs to be treated securely because anyone with it can generate the one-time-passwords that I’m using for multi-factor authentication.
Now if I break another YubiKey, or brick my phone, I can always generate codes using the secret key, or easily re-add it to my new phone. But also, now a new option is open for me: I can programmatically generate the OTP tokens.
(This article is not security advice, I’m not qualified to give that, but again, be careful where you store your MFA secret key or what’s the point of having it!)
Side Note: You Shouldn’t Use SMS as a Authentication Factor
In the past, the most common form of 2FA/MFA was SMS based one-time codes. This form of auth is simple to use, since people have their phones on them all the time. But it has a severe disadvantages in that SIM Swapping can be used by criminals to social engineer the phone company into letting them take control of your phone number. If they do this, they can intercept your texts, and all is lost.
For that reason, if security matters its best to avoid SMS based MFA.
Generating TOTP Tokens Programmatically
Here is a thing I learned. If you have your secret key, it’s straightforward to do what google authenticator does, and generate a token. oathtool is a tool for doing this and you can install it with brew on a mac:
brew install oathtoolOr use whatever package manager is right for you ( sudo apt install oathtool … ). And then you can generate a time-based one-time password (totp) like this:
oathtool -b --totp "{secret}"628254You can also do this in Python:
#!/usr/bin/python3
import pyotp
for name, code in (
('AWS MFA', 'secret')
):
totp = pyotp.TOTP(code)
print('%s: %s' % (name, totp.now()))But you don’t want to stop there. You’d need a way to retrieve the key from somewhere safe.
Retrieving the MFA Key
So here’s what you do.
You’re going to want to store you MFA Key somewhere secure, and not just keep it in a python script, or copy and paste it into your terminal. Because then it might end up in your .history file.
I’m using LastPass, so I can install their CLI tool (lpass) and do something like this:
#!/bin/bash
mfa(){
MFA_KEY="$(lpass show {entry_ID} --json | jq -r '.[].password')"
oathtool -b --totp "$MFA_KEY"
}And then I can get my MFA token like this
$ lpass login usename
...$ mfa
654334This strategy will also work with 1Password, who’s CLI tool is more fully featured. And also, you can store your MFA token in Earthly secrets, a popular choice here at Earthly. You can even store it directly on your YukiKey. That solution is a little bit more work, but if you crush your key like I did, you can get a new one and add your MFA token back.
So now you know what I know about MFA secret keys and how to store them, and use them to generate tokens and time-based one-time passwords for authentication.
Earthly makes CI/CD super simple
Fast, repeatable CI/CD with an instantly familiar syntax – like Dockerfile and Makefile had a baby.









