CI/CD Security: Challenges and Best Practices
We’re Earthly. We make building software simpler and therefore faster using containerization. It’s an ideal tool for boosting the security and efficiency of your CI/CD pipelines. Check it out.
In today’s fast-paced world of software development, speed, and agility are important to stay ahead of the competition. Continuous Integration and Continuous Deployment (CI/CD) have emerged as the go-to methodologies to achieve this goal. CI/CD is a practice that allows developers to continuously integrate and deploy their code changes into production, enabling them to rapidly deliver features and updates to their users.
However, with the speed and efficiency of CI/CD comes the risk of security breaches. As the software development process becomes more automated, security must be integrated into every stage of the pipeline to mitigate these risks. CI/CD security is crucial to ensure that software is developed and deployed securely and reliably.
This article will delve into the challenges and risks associated with CI/CD security, best practices for securing the pipeline, code, and infrastructure, and an overview of the tools and technologies available to organizations to ensure their CI/CD process is secure. By the end of this article, you will have a better understanding of the importance of CI/CD security, and the steps necessary to mitigate the risks associated with it.
CI/CD Security Challenges
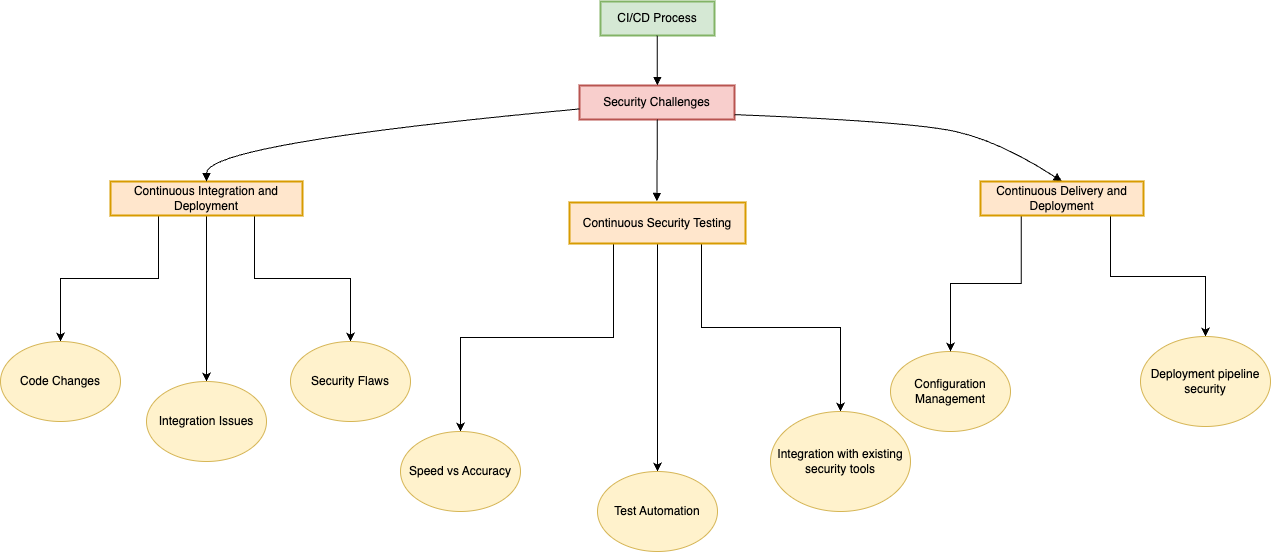
Security is essential in software development, especially in the context of CI/CD. Frequent releases increase the risk of security vulnerabilities, and hackers are always looking for new ways to exploit them. Security threats constantly evolve, so organizations need to integrate security measures throughout the CI/CD pipeline.
This ensures that vulnerabilities are detected and addressed promptly, preventing the deployment of vulnerable applications to production.
There are several challenges and risks associated with CI/CD security, including
Continuous Integration and Deployment Challenges

Code Changes
CI/CD requires frequent code changes, and this creates challenges in maintaining the security of the development process. As code changes are being made, it’s important to ensure that they are thoroughly tested and verified before being integrated into the deployment pipeline. This includes verifying that code changes are compatible with existing code and configurations and that they don’t introduce any new vulnerabilities or security flaws.
For instance, if a developer adds new functionality to an application without properly considering potential security risks, this could introduce new vulnerabilities that could be exploited by attackers. Additionally, changes to configurations, such as access control policies, can inadvertently open up security holes that could be exploited.
To mitigate these risks, it’s important to implement security testing at every stage of the CI/CD pipeline. This includes using automated tools to scan for security vulnerabilities in the code and configurations, as well as conducting manual code reviews to identify potential security issues. Additionally, implementing secure coding practices can help reduce the likelihood of introducing new vulnerabilities with code changes.
In general, the key to ensuring security with CI/CD is to prioritize testing and verification at every stage of the development process. This will help identify and address security issues as soon as possible, reducing the risk of vulnerabilities being introduced into the deployment pipeline.
Integration Issues
Integration issues can occur when different software components are integrated into a system. These components may have different security requirements, and integration issues can lead to security vulnerabilities. It is necessary to ensure that all components are integrated securely, and security requirements are met.
For example, if a third-party library is integrated without proper security checks, it can introduce security vulnerabilities in the software. To address this, developers should ensure that third-party libraries and components are thoroughly tested for security vulnerabilities before integration.
Security Flaws
Security flaws can occur at any stage of the CI/CD pipeline. This can happen when developers accidentally introduce vulnerabilities into the code, or when the system’s infrastructure is not secure. Hackers can exploit these vulnerabilities to gain access to the system and steal sensitive data or cause damage to the system.
For instance, a common security flaw is when a developer includes a hard-coded password or API key in the code. This could give unauthorized users access to the system, leading to potential data breaches. To mitigate these risks, organizations should implement security measures such as multi-factor authentication, access controls, and encryption.
Continuous Security Testing Challenges

Speed vs. Accuracy
One of the biggest challenges with continuous security testing is finding the right balance between speed and accuracy. While it’s important to test code changes as quickly as possible, it’s also important to ensure that the testing is accurate and thorough.
Test Automation
Test automation is an essential component of the CI/CD pipeline as it helps to balance the need for speed and accuracy in software development. However, it can also introduce security concerns if not properly designed and secured. For example, automated tests that do not include security checks may miss potential vulnerabilities in the application. Additionally, a poorly secured automated testing framework can become a target for attackers, compromising the entire pipeline.
To address these concerns, it’s essential to integrate security testing and vulnerability detection into the automated testing process. This involves incorporating security testing tools and practices into the test automation framework to ensure that all code changes are thoroughly evaluated for security risks. By doing so, organizations can identify and fix security vulnerabilities early in the development process, reducing the likelihood of security incidents in the production environment.
Integration With Existing Security Tools
Integrating security testing into existing CI/CD pipelines and tools can also be a challenge for several reasons. One reason is that security tools may not be designed to work seamlessly with existing development tools and processes. This can lead to compatibility issues and disruptions in the pipeline, which can ultimately slow down development and reduce productivity.
Another challenge is that many security tools require significant customization and configuration to meet the specific needs of the organization. This can be a time-consuming and complex process and may require dedicated resources to manage and maintain the integration.
Finally, organizations may face challenges in integrating security testing into their existing development culture and processes. For example, some developers may view security testing as an unnecessary hurdle that slows down development, rather than an essential component of a secure software development lifecycle. Addressing this challenge requires education and training to help developers understand the importance of security testing and how it can be integrated seamlessly into their existing workflows.
Continuous Delivery and Deployment Challenges
Configuration Management
This is another important component of CI/CD security, as misconfigured systems can potentially leave the system vulnerable to attacks. Ensuring that configurations are properly set up and secured can help reduce the risk of security breaches.
Infrastructure as Code(IAC)
IAC is a technique for managing and provisioning IT infrastructure through machine-readable definition files, rather than manually configuring individual systems. IAC allows for the automation of the entire infrastructure lifecycle, including provisioning, configuration, and deployment, reducing the risk of human error and inconsistencies in configuration.
Popular tools and frameworks for IAC include Terraform, Ansible, Puppet, and Chef. These tools enable developers to define infrastructure configurations using code and manage infrastructure changes through version control systems, which can be integrated into the CI/CD pipeline. Additionally, IAC tools often include built-in security features and allow for the enforcement of security policies, such as access control, as code, helping to ensure that infrastructure is configured securely from the beginning.
Deployment Pipeline Security
This is another essential component of CI/CD security. This includes ensuring that deployment configurations are properly set up with specific security measures, such as SSL/TLS encryption and secure ports for communication. Access controls must be implemented to prevent unauthorized access, including user authentication and authorization, network segmentation, and firewalls. Additionally, it’s important to have comprehensive monitoring and logging in place to detect and respond to any security breaches promptly. This can involve using security information and event management (SIEM) tools to monitor activity across the deployment pipeline and alert security teams to potential threats. By addressing these specific concerns, organizations can help to mitigate the risks associated with deploying code in a fast-paced and automated CI/CD environment.
Best Practices for CI/CD Security
When it comes to CI/CD security, several best practices can help ensure your pipeline and code are safe from security threats. Here are some of the most important steps you can take:

Securing the Pipeline
The CI/CD pipeline is an essential part of the software development lifecycle, responsible for automating the build, test, and deployment processes. However, it’s important to ensure that the pipeline is secure from unauthorized access or malicious attacks.
One best practice for securing the CI/CD pipeline is to enforce authentication and authorization for all users and components that interact with it. This means ensuring that users and components are granted access only to the resources that they require and no more. An example of how to enforce authentication and authorization is by using JSON Web Tokens (JWTs) to protect API endpoints.
Similarly, when setting up a CI/CD pipeline using GitHub Actions, you can enforce authentication and authorization to protect the pipeline from unauthorized access or malicious attacks. This can be achieved by generating and using access tokens, which can be granted to users or components that require access to the pipeline. Access tokens can be generated using a secure method and can be revoked or expired when no longer needed.
Here’s an example of how to implement an authentication middleware in a GitHub Actions pipeline using JWTs:
name: My CI/CD Pipeline
on:
push:
branches:
- main
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Authenticate
id: auth
uses: jwt-actions/authenticate@v1
with:
token: $
- name: Build and Deploy
if: steps.auth.outputs.valid == 'true'
run: |
# Perform build and deployment actions hereIn this example, the pipeline runs on a push to the main branch, and the build job is executed on an Ubuntu machine. The first step checks out the code from the repository, and the second step authenticates the user or component using an access token stored in GitHub Secrets. The access token is passed to the jwt-actions/authenticate action, which verifies the token’s authenticity using a secret key.
If the token is valid, the valid output variable is set to true, and the build and deployment actions are executed in the final step. If the token is invalid, the valid output variable is set to false, and the build and deployment actions are skipped.
By enforcing authentication and authorization in your CI/CD pipeline, whether it’s a custom pipeline or using GitHub Actions, you can ensure that only authorized users and components have access to the pipeline and prevent unauthorized access or malicious attacks.
Securing the Code Repository
The code repository is another important component of the CI/CD process. It contains the source code for the application, and any vulnerabilities or weaknesses in the repository can lead to security breaches.
One way to secure the code repository is by implementing access controls and authentication mechanisms. For example, you can use Git’s access control mechanisms to restrict access to the repository and require users to authenticate before they can push changes to the repository.
To set up access controls in Git, you can create a .htaccess file in the repository’s root directory and add the following lines:
AuthType Basic
AuthName "Restricted Access"
AuthUserFile /path/to/htpasswd
Require valid-userThis will prompt users to enter a username and password before they can access the repository. The htpasswd file contains a list of usernames and encrypted passwords, and can be generated using the htpasswd command-line tool. Here’s an example:
htpasswd -c /path/to/htpasswd aliceThis will create a new htpasswd file and add a user called Alice. You can add additional users by running the htpasswd command without the -c option.
In addition to access controls, you can also use Git’s built-in cryptographic features to sign commits and tags, which helps ensure their integrity and authenticity. To sign a commit, you can use the -S option when committing changes:
git commit -S -m "Add new feature"This will prompt you to enter your GPG passphrase and sign the commit using your private key. You can also configure Git to always sign your commits by adding the following line to your .gitconfig file:
[commit]
gpgsign = trueBy implementing access controls and cryptographic features in your code repository, you can help ensure the security and integrity of your codebase, and reduce the risk of unauthorized access or tampering.
To learn more about GitHub access controls, check out the documentation.
Implementing Security Testing in the Pipeline
One of the best practices for implementing security testing in the pipeline is to use automated security testing tools such as OWASP ZAP or SonarQube. This ensures that security vulnerabilities are identified and resolved as early as possible in the development cycle. Here is an example of how to use OWASP ZAP in a pipeline:
# First, download and start OWASP ZAP
wget https://github.com/zaproxy/zaproxy/releases/download/v2.12.0/ZAP_2.12.0_Crossplatform.zip
unzip ZAP_2.12.0_Crossplatform.zip
cd ZAP_2.12.0
./zap.sh -daemon -port 8080 -host 127.0.0.1
# Next, configure your pipeline to run OWASP ZAP
# For example, you can add the following command to your pipeline script:
npm install -g zaproxy
zaproxy start -port 8080 -config api.disablekey=true -daemon
# Then, run your tests and scan your application with OWASP ZAP
npm run test
zaproxy quick-scan -u http://localhost:3000 -l High -r report.html
# Finally, stop OWASP ZAP
zaproxy shutdownThis example shows how to download and start OWASP ZAP, configure it to run in a pipeline, and scan an application for security vulnerabilities. The -l flag sets the alert level (e.g. High, Medium, Low) and the -r flag specifies the output file for the report. The report generated by OWASP ZAP can be used to identify and fix security vulnerabilities in the application.
Monitoring the Pipeline for Security Breaches

The pipeline is constantly evolving, making it susceptible to potential security breaches. To maintain a secure CI/CD process, continuous monitoring of the pipeline for security breaches is essential. You can achieve this by setting up alerts and notifications for suspicious activities and implementing a robust logging system that tracks all pipeline activity.
This can be achieved by using a logging framework such as Winston in a Node.js environment. Winston provides a simple and scalable logging solution that can be easily integrated into the pipeline.
Here is an example of how to use Winston to log pipeline activity in Node.js:
const winston = require("winston");
const { createLogger, format, transports } = winston;
const { combine, timestamp, label, printf } = format;
const logger = createLogger({
level: "info",
format: combine(
label({ label: "pipeline" }),
timestamp(),
printf(({ level, message, label, timestamp }) => {
return `${timestamp} [${label}] ${level}: ${message}`;
})
),
transports: [
new transports.Console(),
new transports.File({ filename: "pipeline.log" }),
],
});
// Example of logging pipeline activity
logger.info("Starting pipeline...");
// Some pipeline code here
logger.info("Pipeline completed successfully");In the example above, the createLogger function is used to create a logger instance that logs messages at the info level or higher. The format function is used to specify the format of the log messages, which includes a timestamp, label, log level, and message.
The logger instance is configured to log messages to the console and to a file called pipeline.log. In the example, the logger is used to log the starting and completion of the pipeline, but it can be used to log any activity that needs to be monitored for security breaches.
By implementing a logging system like this, pipeline activity can be easily monitored and audited for security breaches.
Securing the Infrastructure
To enforce access control policies in the infrastructure, an example of best practice is to use role-based access control (RBAC). This involves defining roles with specific sets of permissions and assigning those roles to users or groups.
For example, in an AWS environment, you can use AWS Identity and Access Management (IAM) to manage access to resources. You can create an IAM role with a specific set of permissions and then assign that role to a user or group. This ensures that users only have access to the resources they need to perform their job functions and nothing more.
Here’s an example IAM policy that enforces RBAC:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowEC2",
"Effect": "Allow",
"Action": [
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:TerminateInstances",
"ec2:DescribeInstances"
],
"Resource": "*"
},
{
"Sid": "AllowS3",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:DeleteObject",
"s3:ListBucket"
],
"Resource": ["arn:aws:s3:::my-bucket/*", \
"arn:aws:s3:::my-bucket"]
},
{
"Sid": "DenyAll",
"Effect": "Deny",
"Action": "*",
"Resource": "*"
}
]
}In this example, the policy allows the user to start, stop, and terminate EC2 instances and perform certain actions on an S3 bucket but denies all other actions. The policy can be assigned to a user or group to enforce RBAC.
Securing the Code
To ensure secure code, it is important to implement secure coding practices, such as using secure coding standards, testing for vulnerabilities, and managing sensitive data.
One recommended practice is to use a code review process that includes security testing. Code reviews can help to identify potential vulnerabilities and weaknesses in the code before it is merged into the codebase. In addition, utilizing code analysis tools to scan for security issues can help identify potential security risks. By incorporating both code review and analysis tools, developers can ensure that their code is secure and free from vulnerabilities and weaknesses, reducing the risk of a data breach.
By following these best practices, you can help ensure that your CI/CD pipeline and code are secure from the start.
CI/CD Security Tools and Technologies
Now that you understand the importance of CI/CD security and the best practices to follow, it’s time to explore the tools and technologies available for securing your pipeline. There are several tools and techniques that you can use to ensure that your CI/CD pipeline is secure. Let’s explore some of them below:
Static Code Analysis
Static code analysis tools play an important role in ensuring the security of your codebase. They use various techniques to analyze your code for potential vulnerabilities, such as hardcoded secrets or vulnerable libraries. By integrating these tools into your CI/CD pipeline, you can catch any security issues early in the development process, before they make it into production.
However, it’s important to note that while static code analysis can help detect certain security issues, it’s not a silver bullet solution. It should be used in conjunction with other security measures, such as dynamic testing and manual code reviews, to provide comprehensive security coverage for your application.
Dynamic Application Security Testing (DAST)
DAST tools are an essential component of a comprehensive application security testing strategy. Unlike static code analysis tools, which analyze code without running the application, DAST tools test the security of an application in a running environment.
These tools simulate attacks and identify vulnerabilities that an attacker could exploit, giving you an accurate picture of your application’s security posture. By using DAST tools, you can identify and fix any security issues in your application before it is deployed, reducing the risk of a successful attack in production.
However, it’s important to note that DAST tools are not foolproof and may not catch all vulnerabilities, so it’s recommended to use them in conjunction with other security testing tools and best practices.
Interactive Application Security Testing (IAST)
IAST tools analyze an application’s code and runtime behavior to identify security vulnerabilities. They can detect issues like SQL injection and Cross-Site Scripting (XSS) attacks. This is important because it can detect security issues that may be missed by other testing methods, and it provides more detailed information about the root cause of any issues found. IAST is best used during the testing phase when the application is in a more complete state, and can also be used in production to continuously monitor for vulnerabilities.
Choosing the Right Tools for Your Organization
Choosing the right security tools for your organization can be a daunting task. Here are some factors to consider when selecting security tools for your CI/CD pipeline:
Compatibility With Your Stack
When it comes to compatibility, it’s important to look for tools that support your programming languages, frameworks, and other technologies. For example, if you’re developing a web application with a frontend built in React and a backend built in Node.js, you might want to consider a tool like ESLint for static code analysis or the OWASP ZAP proxy for dynamic application security testing, both of which have plugins or integrations for both React and Node.js.
Ease of Integration
Selecting tools that are easy to integrate into your existing CI/CD pipeline can save you a lot of time and effort. One example of a tool with easy integration is GitLab’s built-in DAST scanner, which can be enabled with just a few clicks in the GitLab CI/CD pipeline configuration. Other tools, like dependency checkers such as Snyk or WhiteSource, offer integrations with popular package managers like npm and can be run as part of your CI/CD pipeline with minimal setup.
Cost
When considering the cost of security tools, it’s important to weigh the benefits against the price tag. Some free or open-source tools, like SonarQube or OWASP Dependency-Check, can provide significant value without any monetary investment. However, some paid tools like Veracode or Checkmarx offer additional features and support that may be worth the investment for larger organizations or high-risk applications.
These are just a few examples of the many security tools available and how they might fit into your CI/CD pipeline. The most important thing is to carefully evaluate the needs of your organization and the specific applications you’re developing, and choose the tools that will provide the most value and best meet your requirements.
Integration With CI/CD Pipeline
Integrating security tools into your CI/CD pipeline is essential for detecting and fixing security issues. Here are some steps you can take to integrate security tools into your pipeline:
Integrate The Tools Into Your Pipeline
The first step is to integrate the security tools you choose into your pipeline. This integration should be seamless, and the tool should not interfere with the existing workflow.
Configure the Tools
Once the tools are integrated, you need to configure them to suit your needs. You can configure the tools to run specific tests, set up alerts for critical issues, and more.
Automate the Testing Process
Automating the testing process can save time and resources. By automating tests, you can ensure that they run consistently and that you catch any issues as soon as possible.
Here’s an example of how you can integrate static code analysis into your pipeline using the open-source tool SonarQube:
Download the SonarQube package from the official website.
Unzip the downloaded package to a directory on your system.
Install a Java Runtime Environment (JRE) if one is not already installed.
Configure the database connection in SonarQube by editing the
sonar.propertiesfile located in theconfdirectory. For example, if you are using MySQL, you would uncomment the following line and provide your database credentials:#sonar.jdbc.url=jdbc:mysql://localhost:3306/sonar?useUnicode=true&characterEncoding=utf8&rewriteBatchedStatements=true&useConfigs=maxPerformance #sonar.jdbc.username=root #sonar.jdbc.password=rootStart the SonarQube server by running the bin/[your-os]/sonar.sh start command in the root directory of the extracted package. For example, on Linux or macOS, you would run:
./bin/linux-x86-64/sonar.sh startVerify that SonarQube is running by accessing the web interface at
http://localhost:9000(assuming you have not changed the default port).
Note that these are general steps and may vary depending on your specific setup and requirements. It is recommended to refer to the official SonarQube documentation for detailed installation instructions.
Conclusion
CI/CD security is crucial to secure and efficient software development and deployment. It reduces risk of breaches, enhances team collaboration, and improves software quality. However, it does face challenges like code changes, integration issues, and test automation.
Best practices to tackle these issues include securing the CI/CD pipeline and the code repository, implementing access control policies, monitoring security-focused logs, and managing secure configurations.
Using security tools and technologies like static code analysis, DAST, and IAST can also enhance CI/CD security. Factors such as integration with the pipeline, user-friendliness, and scalability should be considered when choosing these tools.
In essence, prioritizing CI/CD security and using the right practices and tools can mitigate risks and enhance software quality. And if you’re looking for a build automation tool that aligns well with your secure CI/CD practices, you might want to give Earthly a look!
Earthly makes CI/CD super simple
Fast, repeatable CI/CD with an instantly familiar syntax – like Dockerfile and Makefile had a baby.










